Original Post Date: February 10, 2023
Recent news reminds us that vulnerabilities persist in critical infrastructure platforms targeted by financially motivated and state-sponsored espionage threat actors. We’re constantly hearing about the exploitation of old and new vulnerabilities as part of cyberattacks. While vulnerability management may be challenging, we must be vigilant and look for ways to improve our cybersecurity defenses. Implementing external attack surface management (EASM), an integral part of vulnerability management, can significantly improve your cybersecurity posture and reduce your organization’s cybersecurity risk.
What is External Attack Surface Management (EASM)?
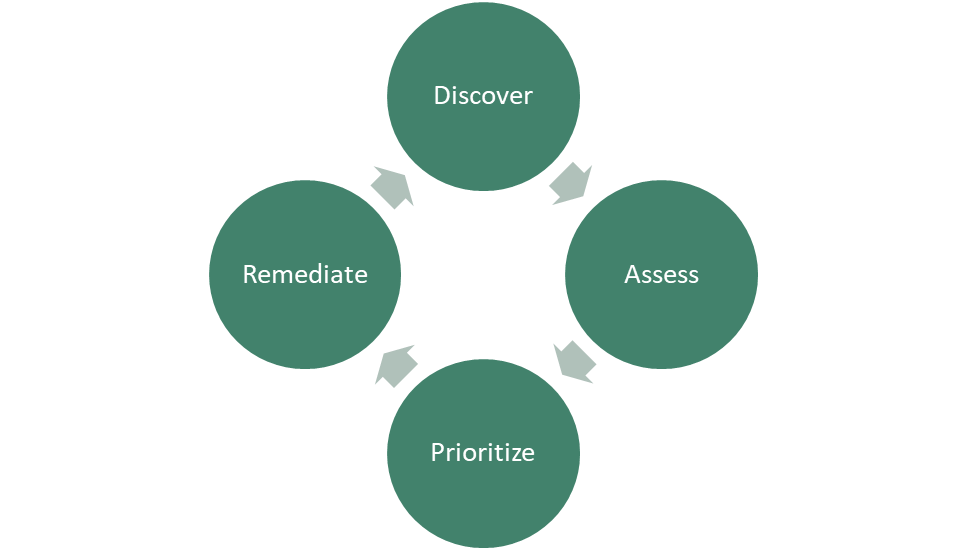
EASM is the continuous discovery/inventory, assessment, prioritization, and remediation of an organization’s Internet-facing assets. These Internet-facing assets are the organization’s digital attack surface. EASM helps organizations identify and manage cybersecurity risks associated with their digital attack surface.
An organization’s digital attack surface includes but is not limited to the following:
- Servers
- Operating Systems
- IoT Devices
- Network Devices
- Domain Names
- TLS Certificates
- SaaS Applications
- Cloud-based Workloads
- Assets Integrated with Third Parties
EASM enables organizations to continuously discover and assess the risk of their digital attack surface and prioritize and plan the remediation of those risks.
Why is EASM Important?
Cybersecurity defenders and vulnerability management teams must have complete visibility into their organization’s digital attack surface to monitor, protect, and defend against future attacks. Visibility requires an up-to-date and prioritized inventory of assets to monitor, assess, and remediate.
Reconnaissance is often the first step performed as part of an attack or red team assessment and is the first step in the Cyber Kill Chain. Organizations should perform continuous discovery to identify gaps in their visibility of assets exposed to the Internet. There are several ways to discover Internet-facing assets, most notably by using an EASM tool/platform.
One situation where EASM is of immense value is during the merger and acquisition (M&A) process. EASM provides organizations visibility into the digital attack surface and cybersecurity risks associated with the company they are planning to acquire. Digital attack surface visibility during the M&A process is critical to defending against new and previously unknown threats. Armed with EASM intelligence of new cybersecurity risks, leadership can make evidence-based strategic decisions.
Beyond the Basics of EASM
Continuous vulnerability scanning should be part of/integrated with any EASM solution. It is a huge win to discover a new asset, immediately scan it for vulnerabilities, and prioritize its remediation based on data classification. Be sure to keep this in mind when (re)evaluating an EASM solution.
What’s even better is if an EASM solution includes other information-gathering capabilities, such as:
- Account Exposure
- Typosquatted Domains (sometimes referred to as Brand Protection)
- Data Leak Discovery
- Metadata Exposure
Products that integrate these capabilities go far above and beyond typical EASM solutions and, IMHO, are worth careful consideration.
EASM has its challenges. However, organizations can work to overcome challenges. EASM is a tool that every organization should implement.

